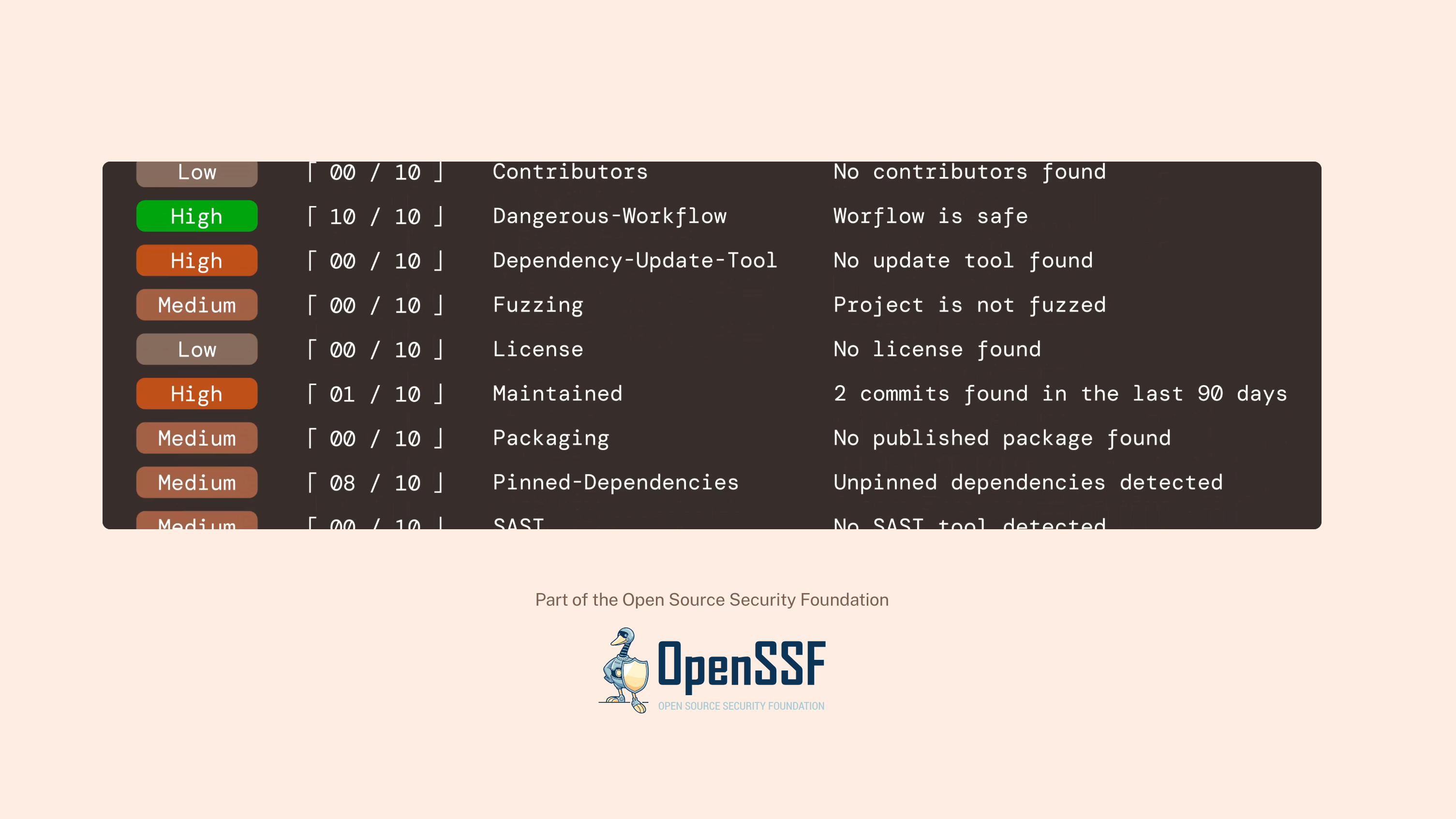
I authored a tutorial on govulncheck, a vulnerability scanner created for the Google programming language Go. This guide, published on the Go documentation site, covers installation and usage instructions for developers aiming to enhance the security posture of their projects.
Working with several senior team members, I revamped the landing page for the Go Security website. The old version of the landing page was bare-bones and had not been updated for years, so it did not reflect the most relevant information. The new landing page acts as a hub for people seeking to explore the security-related content on the site.
This tutorial shows developers how to leverage the VS Code Go extension to scan for vulnerabilities directly from their IDE. By incorporating vulnerability scanning into their workflow in this way, they can proactively detect and mitigate security risks during development. The screenshots in the tutorial make troubleshooting easier for developers following along, allowing them to easily determine if they are seeing the correct mouseover elements.
This Best Practices Guide offers actionable recommendations on how to boost the security posture of their projects in an efficient, sustainable way. I wrote the document after detailed consultations with engineers on the Go Security team, making sure the tips I included had an appropriate balance of detail and conciseness for new developers.
In collaboration with a Go Security tech lead, I wrote a summary of Go’s vulnerability management system. The page serves as a central hub for developers seeking guidance on prioritizing security in their projects, ultimately fostering a safer and more resilient Go ecosystem. We decided to add a graphic when we realized that including the pipeline’s many components in a concise writeup was proving challenging. The three-part visualization, which I designed, provides a digestible breakdown of the pipeline.